1EdTech TrustEd Apps Security Practices Rubric
Spec Version 1.0
| Document Version: | 1.0 |
| Date Issued: | Nov 3rd, 2023 |
| Status: | This document is for review and adoption by the 1EdTech membership. |
| This version: | https://www.imsglobal.org/spec/Rubric/v1p0/ |
| Latest version: | https://www.imsglobal.org/spec/Rubric/latest/ |
| Errata: | https://www.imsglobal.org/spec/Rubric/v1p0/errata/ |
IPR and Distribution Notice
Recipients of this document are requested to submit, with their comments, notification of any relevant patent claims or other intellectual property rights of which they may be aware that might be infringed by any implementation of the specification set forth in this document, and to provide supporting documentation.
1EdTech takes no position regarding the validity or scope of any intellectual property or other rights that might be claimed to pertain implementation or use of the technology described in this document or the extent to which any license under such rights might or might not be available; neither does it represent that it has made any effort to identify any such rights. Information on 1EdTech's procedures with respect to rights in 1EdTech specifications can be found at the 1EdTech Intellectual Property Rights webpage: http://www.imsglobal.org/ipr/imsipr_policyFinal.pdf .
The following participating organizations have made explicit license commitments to this specification:
| Org name | Date election made | Necessary claims | Type |
|---|---|---|---|
| Instructure, Inc. | June 12, 2023 | No | Royalty-free RAND License |
Use of this specification to develop products or services is governed by the license with 1EdTech found on the 1EdTech website: http://www.imsglobal.org/speclicense.html.
Permission is granted to all parties to use excerpts from this document as needed in producing requests for proposals.
The limited permissions granted above are perpetual and will not be revoked by 1EdTech or its successors or assigns.
THIS SPECIFICATION IS BEING OFFERED WITHOUT ANY WARRANTY WHATSOEVER, AND IN PARTICULAR, ANY WARRANTY OF NONINFRINGEMENT IS EXPRESSLY DISCLAIMED. ANY USE OF THIS SPECIFICATION SHALL BE MADE ENTIRELY AT THE IMPLEMENTER'S OWN RISK, AND NEITHER THE CONSORTIUM, NOR ANY OF ITS MEMBERS OR SUBMITTERS, SHALL HAVE ANY LIABILITY WHATSOEVER TO ANY IMPLEMENTER OR THIRD PARTY FOR ANY DAMAGES OF ANY NATURE WHATSOEVER, DIRECTLY OR INDIRECTLY, ARISING FROM THE USE OF THIS SPECIFICATION.
Public contributions, comments and questions can be posted here: http://www.imsglobal.org/forums/ims-glc-public-forums-and-resources .
© 2023 1EdTech™ Consortium, Inc. All Rights Reserved.
Trademark information: http://www.imsglobal.org/copyright.html
Abstract
The existing TrustEd Apps vetting process has been very valuable to our members. The TrustEd Apps Security Practice Rubric and process has been developed to meet the increasing needs of our institutional members who need additional information to understand and mitigate security risks within their teaching and learning environment to accelerate their procurement processes. The scope of this rubric is course level tools that have access to a smaller scope of data and does not include enterprise level tools It focuses on the essential needs of higher education institutions.
Educational applications provide content and tools to help students learn. Educational applications are created and managed by suppliers. Suppliers manage the identity of the individuals accessing the system and the data that they generate. However, there are many factors that need to be considered to ensure that each application used by institutions is appropriate for students. The student’s privacy, data security, or other safety considerations implemented by suppliers when developing educational tools may not match the needs of an institution, thus it is the responsibility of the institution to ensure required security safeguards are in place.
Educational institutions are required to ensure suppliers meet their institutional security requirements. This has created an environment where institutions are vetting applications independently of other institutions, often with their own unique but similar questions. This separate and independent evaluation places a burden on institutions and suppliers to timely and cost-effectively adopt new technologies. This TrustEd Apps Security Practices Rubric specification provides suppliers a method to communicate their policies and practices in a consistent format. Institutions can leverage this information, reducing the time, manpower, and cost required to vet applications while ensuring all considerations are consistently met. Within the rubric, 1EdTech has identified four areas that provide a consistent format so institutions can have the additional information needed to mitigate security risks within their teaching and learning environment and accelerate their procurement processes.
This rubric has been developed to reference the EDUCAUSE’s HECVAT LITE rubric, so that institutions and suppliers can easily transfer their responses if they need more information than the 1EdTech TrustEd Apps Security rubric provides.
Scope and Context
In Scope
The scope of this task force was to enable a standard self-vetting process that incorporates the use of the rubric and a method of describing a supplier’s policies, procedures, and systems to identify their security posture. The goal of this process is to enable an open line of communication for suppliers and districts/institutions to work together to provide an accurate review of the organization's products.
The open collaboration between districts/institutions and suppliers also promotes transparency that helps members understand the various components of security policies and practices and why they are necessary. As a result of this process, users will be able to make informed decisions about the digital resources they use. This app vetting rubric defines a standard set of evaluation questions, grouped by category, with indicators to establish whether an app meets expectations or not.
This rubric is designed to be used for tools with limited access to data used in the teaching and learning environment. Typically, these tools are integrated via LTI. The rubric can also be used to review the many web based tools available to teachers and students. Because of the focus of this rubric we do not recommend using this as the sole evaluation tool for larger enterprise- level adoptions. This rubric is a scaled down version of EDUCAUSE’s HECVAT LITE rubric, focusing on the essential needs of higher education institutions.
Out of Scope
The scope of this task did not include providing guidance or standards for enterprise level tools or tools containing HIPAA data and/or PCI data. This rubric does not enable users to make decisions for high risk tools.
This task force acknowledges the critical importance of all parties to secure data and is supportive of the industry security best practices to ensure private data is secured. We also recognize that there are other existing programs and resources available to support a more comprehensive review of a solution’s security practices and procedures.
Use Cases
Most schools, districts and institutions struggle to ensure that their teachers and students are using approved digital resources in the classroom and online. A number of schools and institutions have put in place a process for faculty or teachers to make a request for approval of a digital resource. The subsequent evaluation processes are often too long and inefficient to accommodate faculty or teacher’s “On Demand” needs, in time for their upcoming classes. The 1EdTech TrustEd Apps Security Practices Rubric can supplement these evaluation processes by allowing instructors and staff to get a quick snapshot view of an app's security, providing confidence that the chosen app aligns with the basic requirements for security. Evaluation authorities themselves can use the rubric to get an understanding of a tool's security posture to better know how long it will take them to move through their institutional review process. This also reduces demands on IT and procurement, allowing staff to focus attention on the most promising applications that have the desired security profile or be more realistic when determining a timeframe for implementation
This app vetting rubric also benefits Ed-tech suppliers by helping them avoid countless requests from multiple schools, districts, and institutions for the kind of information that the rubric is meant to address. Without this rubric, suppliers have to commit scarce resources to answer questionnaires, addressing issues very similar to those raised by others. Via the app vetting process, suppliers submit information to 1Edtech using the rubric that is then published for institutional viewing and feedback process. This process promises to ease the supplier's burden of communication allowing them to focus their resources on improving their software and services. The alignment of this rubric with EDUCAUSE’s HECVAT also enables suppliers to easily transfer their answers between the two rubrics. This rubric can also inform Ed-tech suppliers of typical institutional requirements for integration into their digital learning environment.
Structure of This Document
The structure of the rest of this document is:
| Number | Section | Description |
|---|---|---|
| 1. | ABSTRACT | The overview, context, scope and goals outlining the purpose of this TrustEd Apps Security Practices Rubric. |
| 2. | USE CASES | The use cases that are addressed by this TrustEd Apps Security Practices Rubric. |
| 3. | INTRODUCTION to the TrustEd Apps Security Practices Rubric | Description of a rubric including the definition of the evaluation criteria. |
| 4. | THE APP VETTING PROCESS | Description of the process that must be undertaken to complete, revise and maintain an app vetting rubric. |
| 5. | THE RUBRIC | The image and link to the rubric including the questions that must be answered to determine the degree to which the evaluation criteria are achieved. |
Security App Vetting Vocabulary/Terminology
-
Access Control - The process of granting or denying specific requests to 1) obtain and use information and related information processing services and 2) enter specific physical facilities (e.g., federal buildings, military establishments, border crossing entrances). https://csrc.nist.gov/glossary/term/at
-
Attribute Based Access Control (ABAC) - An access control approach in which access is mediated based on attributes associated with subjects (requesters) and the objects to be accessed. Each object and subject has a set of associated attributes, such as location, time of creation, access rights, etc. Access to an object is authorized or denied depending upon whether the required (e.g., policy-defined) correlation can be made between the attributes of that object and of the requesting subject. https://csrc.nist.gov/glossary/term/at
-
At-Rest - The encryption of the data that is stored in the databases and is not moving through networks. https://www.ibm.com/docs/en/strategicsm/10.1.3?topic=security-data-rest-encryption
-
Authentication - Verifying the identity of a user, process, or device, often as a prerequisite to allowing access to resources in an information system. https://csrc.nist.gov/glossary/term/authentication
-
Auto Provision - The ability to deploy information technology or telecommunications services using predefined automated procedures without requiring human interventions. https://www.ericsson.com/en/blog/2019/8/why-is-automated-provisioning-so-important
-
Automated Intrusion Detection System (IDS) - A security service that monitors and analyzes network or system events for the purpose of finding, and providing real-time or near real-time warning of, attempts to access system resources in an unauthorized manner. https://csrc.nist.gov/glossary/term/intrusion_detection_system
-
Automated Intrusion Prevention System (IPS) - A system that can detect an intrusive activity and can also attempt to stop the activity, ideally before it reaches its targets. https://csrc.nist.gov/glossary/term/intrusion_prevention_system
-
Breach - The loss of control, compromise, unauthorized disclosure, unauthorized acquisition, or any similar occurrence where: a person other than an authorized user accesses or potentially accesses personally identifiable information; or an authorized user accesses personally identifiable information for another than authorized purpose. https://csrc.nist.gov/glossary/term/breach
-
Change Management Process (CMP) - A systematic approach to dealing with the transition or transformation of an organization's goals, processes or technologies. The purpose of change management is to implement strategies for effecting change, controlling change and helping people to adapt to change. https://www.techtarget.com/searchcio/definition/change-management
-
CIS Controls - A recommended set of cybersecurity best practices and defensive actions that provide specific and actionable ways to thwart the most pervasive attacks and support compliance in a multiframework environment. https://www.unitrends.com/blog/cis-controls
-
Cloud Service - Any IT services that are provisioned and accessed from a cloud computing provider. This is a broad term that incorporates all delivery and service models of cloud computing and related solutions. Cloud services are delivered over the internet and accessible globally from the internet. https://www.techopedia.com/definition/29017/cloud-services
-
Cyber-Risk Insurance - also referred to as cyber liability insurance coverage (CLIC), is a policy with an insurance carrier to mitigate risk exposure by offsetting costs involved with damages and recovery after a cyber-related security breach or similar event. https://www.csoonline.com/article/3643054/cyber-insurance-explained.html
-
Cybersecurity Framework - A layered structure indicating what kind of programs can or should be built and how they would interrelate. Some computer system frameworks also include actual programs, specify programming interfaces, or offer programming tools for using the frameworks. A framework may be for a set of functions within a system and how they interrelate; the layers of an operating system; the layers of an application subsystem; how communication should be standardized at some level of a network; and so forth. A framework is generally more comprehensive than a protocol and more prescriptive than a structure. https://csrc.nist.gov/glossary/term/framework
-
Data Encryption - translates data into another form, or code, so that only people with access to a secret key (formally called a decryption key) or password can read it. https://www.digitalguardian.com/blog/what-data-encryption
-
Data in Transport - The part of the service related to communication lines from and to the Provider’s Data Center, the Customer’s offices and from or to the Internet also while mobile. https://www.lawinsider.com/dictionary/data-transport
-
Data Input Validation - Confirmation (through the provision of strong, sound, objective evidence) that requirements for a specific intended use or application have been fulfilled (e.g., a trustworthy credential has been presented, or data or information has been formatted in accordance with a defined set of rules, or a specific process has demonstrated that an entity under consideration meets, in all respects, its defined attributes or requirements). https://csrc.nist.gov/glossary/term/validation
-
Data Sanitization - Process to remove information from media such that information recovery is not possible. It includes removing all labels, markings, and activity logs. https://csrc.nist.gov/glossary/term/sanitization
-
Data Separation (Logical) - Separating and storing data in separate logical partitions or storage areas, even if those partitions or storage are on the same physical device. This can be much more cost effective than physical segregation and allows organizations much more flexibility in designing and implementing data access policies. Because all data is physically on the same system, changing data access policies or who can access specific data sets can be done by modifying the logical rules, instead of physically moving data, or changing who has physical access to the systems. https://www.nextlabs.com/what-is-data-segregation/
-
Data Separation (Physical) - Separating and storing data on different physical systems or networks. While this may prevent someone from accessing the data if they don’t have physical access to the systems where it is stored, it also requires the expense of setting up different systems for the data sets that need to be segregated. Data storage regulations may require physical segregation, however, especially in the case where data is not allowed to leave a country’s borders or there are restrictions on sending data to certain countries. By implementing physical separation, organizations can comply with export regulations of this nature. https://www.nextlabs.com/what-is-data-segregation/
-
DevSecOps - DevSecOps stands for development, security, and operations. It's an approach to culture, automation, and platform design that integrates security as a shared responsibility throughout the entire IT lifecycle. https://www.redhat.com/en/topics/devops/what-is-devsecops
-
Disaster Recovery Plan (DRP) - A written plan for processing critical applications in the event of a major hardware or software failure or destruction of facilities. https://csrc.nist.gov/glossary/term/disaster_recovery_plan
-
End User - the ultimate consumer of a finished product. https://www.merriam-webster.com/dictionary/end%20user
-
End-of-Life (EOL) - The OEM will no longer market, sell, or update your equipment after a certain date. https://serviceexpress.com/resources/eol-eosl-tip-sheet/
-
External Audit - Independent review and examination of records and activities to assess the adequacy of system controls, to ensure compliance with established policies and operational procedures. https://csrc.nist.gov/glossary/term/audit
-
Higher Education Community Vendor Assessment Toolkit (HECVAT) - a questionnaire framework specifically designed for higher education to measure vendor risk. Before you purchase a third-party solution, ask the solution provider to complete a HECVAT tool to confirm that information, data, and cybersecurity policies are in place to protect your sensitive institutional information and constituents' PII. https://library.educause.edu/resources/2020/4/higher-education-community-vendor-assessment-toolkit
-
Hosting Provider - A type of IT service provider that provisions and serves a pool of remote, Internet-based IT resources to individuals and organizations for hosting their websites. A hosting service provider delivers hardware, software, storage, network and/or their combined solutions to enable Web hosting services. https://www.techopedia.com/definition/137/hosting-services-provider-hsp
-
Infrastructure as a Service (IaaS) - The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications; and possibly limited control of select networking components (e.g., host firewalls). https://csrc.nist.gov/glossary/term/infrastructure_as_a_service
-
Incident Response Plan - The documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber attacks against an organization’s information systems(s). https://csrc.nist.gov/glossary/term/incident_response_plan
-
Information Security - The protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability. https://csrc.nist.gov/glossary/term/information_security
-
Information Security Principles - Confidentiality, integrity, and availability (CIA) are the core information security principles. Together, these three principles are read as the CIA triad. These three principles help maintain the core requirement of InfoSec for the safe storage, utilization, and transmission of information. https://emeritus.org/in/learn/information-security-and-its-principles/
-
Internal Incident Response Team - An incident response team, also called an incident response unit, is a group responsible for planning for and responding to IT incidents, including cyber attacks, systems failures, and data breaches. https://www.cynet.com/incident-response/incident-response-team-a-blueprint-for-success/
-
Intrusion Detection System (IDS) - IDSs which detect attacks by capturing and analyzing network packets. Listening on a network segment or switch, one network-based IDS can monitor the network traffic affecting multiple hosts that are connected to the network segment. https://csrc.nist.gov/glossary/term/intrusion_detection_system
-
Intrusion Prevention System (IPS) - Intrusion Prevention System: Software that has all the capabilities of an intrusion detection system and can also attempt to stop possible incidents. https://csrc.nist.gov/glossary/term/intrusion_prevention_system
-
ISO 27001 - ISO/IEC 27001 is the international standard for information security. It sets out the specification for an effective ISMS (information security management system). ISO 27001's best-practice approach helps organisations manage their information security by addressing people, processes and technology. https://www.itgovernance.co.uk/iso27001
-
Media Handling Process - To Stop unauthorized release, alteration, deletion, or destruction of information contained in the media. https://info-savvy.com/iso-27001-annex-a-8-3-media-handling/
-
MFA - An authentication system that requires more than one distinct authentication factor for successful authentication. Multifactor authentication can be performed using a multifactor authenticator or by a combination of authenticators that provide different factors. The three authentication factors are something you know, something you have, and something you are. https://csrc.nist.gov/glossary/term/mfa
-
National Institute of Standards and Technology (NIST) - The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary. https://www.ftc.gov/business-guidance/small-businesses/cybersecurity/nist-framework
-
Open Worldwide Application Security Project® (OWASP) - A nonprofit foundation that works to improve the security of software. Through community-led open-source software projects, hundreds of local chapters worldwide, tens of thousands of members, and leading educational and training conferences, the OWASP Foundation is the source for developers and technologists to secure the web. https://owasp.org/
-
Platform as a Service (PaaS) - The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment. https://csrc.nist.gov/glossary/term/platform_as_a_service
-
Policy Based Access Control (PBAC) - A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access privileges users of each role should have. Theoretical privileges are compared to actual privileges, and differences are automatically applied. For example, a role may be defined for a manager. Specific types of accounts on the single sign-on server, Web server, and database management system may be attached to this role. Appropriate users are then attached to this role. https://csrc.nist.gov/glossary/term/policy_based_access_control
-
Payment Card Industry Data Security Standard (PCIDSS) - An information security standard administered by the Payment Card Industry Security Standards Council that is for organizations that handle branded credit cards from the major card schemes. https://csrc.nist.gov/glossary/term/pci_dss
-
Product Lifecycle - The length of time from a product first being introduced to consumers until it is removed from the market. A product’s life cycle is usually broken down into four stages; introduction, growth, maturity, and decline. https://www.twi-global.com/technical-knowledge/faqs/what-is-a-product-life-cycle
-
Product Management - An organizational function that guides every step of a product’s lifecycle — from development to positioning and pricing — by focusing on the product and its customers first and foremost. To build the best possible product, product managers advocate for customers within the organization and make sure the voice of the market is heard and heeded. https://www.atlassian.com/agile/product-management
-
Role Based Access Control - Access control based on user roles (i.e., a collection of access authorizations a user receives based on an explicit or implicit assumption of a given role). Role permissions may be inherited through a role hierarchy and typically reflect the permissions needed to perform defined functions within an organization. A given role may apply to a single individual or to several individuals. https://csrc.nist.gov/glossary/term/role_based_access_control
-
Software as a Service (SaaS) - The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g., web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings. https://csrc.nist.gov/glossary/term/software_as_a_service
-
Security Assessment - The testing and/or evaluation of the management, operational, and technical security controls in an information system to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system. https://csrc.nist.gov/glossary/term/security_assessment
-
Security Framework - A compilation of state-mandated and international cybersecurity policies and processes to protect critical infrastructure. It includes precise instructions for companies to handle the personal information stored in systems to ensure their decreased vulnerability to security-related risks. https://www.techslang.com/definition/what-is-a-security-framework/
-
Security Posture - The security status of an enterprise’s networks, information, and systems based on information security resources (e.g., people, hardware, software, policies) and capabilities in place to manage the defense of the enterprise and to react as the situation changes. https://csrc.nist.gov/glossary/term/security_posture
-
SOC 2 - SOC 2 is a voluntary compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. https://www.checkpoint.com/cyber-hub/cyber-security/what-is-soc-2-compliance/
-
Software - Computer programs and data stored in hardware - typically in read-only memory (ROM) or programmable read-only memory (PROM) - such that the programs and data cannot be dynamically written or modified during execution of the programs. https://csrc.nist.gov/glossary/term/software
-
Source IP Address - The IP address of the outgoing switch interface on which the client is communicating with the server. https://www.arubanetworks.com/techdocs/AOS-CX/10.10/HTML/fundamentals_83xx-10000/Content/Chp_IfaceCfg/sin-sou-ip-add-10.htm
-
Single Sign-On (SSO) - Is an identification method that enables users to log in to multiple applications and websites with one set of credentials. SSO streamlines the authentication process for users. It takes place when a user logs in to an application and is automatically signed in to other connected applications, regardless of the domain, platform, or technology they are using. This eases the management of multiple usernames and passwords across various accounts and services. https://www.fortinet.com/resources/cyberglossary/single-sign-on
-
Stateful Packet Inspection Firewall (SPI) - Packet filtering that also tracks the state of connections and blocks packets that deviate from the expected state. https://csrc.nist.gov/glossary/term/stateful_inspection Static Application Security Testing - Static application security testing (SAST), or static analysis, is a testing methodology that analyzes source code to find security vulnerabilities that make your organization's applications susceptible to attack. SAST scans an application before the code is compiled. It's also known as white box testing. https://www.synopsys.com/glossary/what-is-sast.html
-
Static Code Analysis - The act of reverse-engineering the malicious program to understand the code that implements the software behavior. For example, when looking at compiled programs, the process involves using a disassembler, a debugger, and perhaps a decompiler to examine the program’s low-level assembly or byte-code instructions. A disassembler converts the instructions from their binary form into the human-readable assembly form. A decompiler attempts to recreate the original source code of the program. A debugger allows the analyst to step through the code, interacting with it, and observing the effects of its instructions to understand its purpose. https://csrc.nist.gov/glossary/term/code_analysis
-
System Development - The scope of activities associated with a system, encompassing the system’s initiation, development and acquisition, implementation, operation and maintenance, and ultimately its disposal. https://csrc.nist.gov/glossary/term/system_development_life_cycle
-
Timestamp - A token or packet of information that is used to provide assurance of timeliness; the timestamp contains timestamped data, including a time, and a signature generated by a Trusted Timestamp Authority (TTA). https://csrc.nist.gov/glossary/term/timestamp
-
Web Application Firewall - A firewall that uses stateful protocol analysis to analyze network traffic for one or more applications. https://csrc.nist.gov/glossary/term/application_firewall
Key Concepts & Elements
This rubric is designed to gather information about a supplier’s base level security policies, procedures, and systems to identify their security posture. Each institution and school district has a responsibility to ensure that the supplier solutions meet institutional security requirements. This rubric is designed to provide a concise and consistent tool to provide insight for institutions to decide how they would like to proceed with their procurement process.
What is a Rubric and how is it being used here?
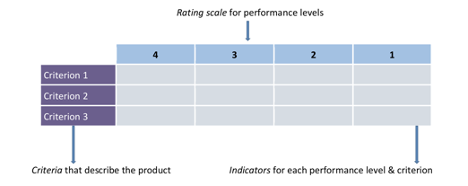
A Rubric is a scoring guide used to evaluate performance, a product, or a project. Typically, it has three parts: 1) performance criteria, 2) rating scale, and 3) indicators.

Figure 1 Source:https://facultyinnovate.utexas.edu/sites/default/files/build-rubric.pdf
This TrustEd Apps Security specification defines a Rubric that institutions and school districts can use for enhanced App Vetting. Members of the 1EdTech community pooled their collective evaluation criteria into a common rubric for reviewing 3rd party apps (members also looked at criteria set by other organizations that vet applications for their security practices). These collective criteria cover a basic set of questions that suppliers need to provide answers and evidence to when self assessing their applications.
With a common set of evaluation criteria, each institution or school district can specify their requirements in a consistent way making it easier for suppliers to self-assess their apps. In addition, when responding to requirements coming from each of their educational customers, suppliers will also have a consistent way to document their own apps’ behavior in each of the required areas.
TrustEd Apps Security Practices Rubric
While the rubric is a starting point for reviewing the security practices of a digital resource or application, this enables open communication between 1EdTech suppliers and districts/institutions to work together to provide an accurate self review of the suppliers products. The open collaboration between districts/institutions and suppliers also promotes transparency that helps members understand the various components of security policies, practices, and procedures and why they are necessary.
How is this rubric different from other vetting instruments such as HECVAT?
The Higher Education Community Vendor Assessment Toolkit (HECVAT 3.04) is used within the Higher Education community to assess suppliers of cloud infrastructure services. The most recent version of the HECVAT available when writing this document (v3.04) covers many aspects of supplier-provided services such as company history, business continuity plan, change management process, physical security, firewalls, and networking. These aspects are important to establish a basis for supplier relationships, contracts with institutional specific procurement requirements, and so on. However, the volume of requests for teaching and learning tools to be integrated into the learning environment results in a large burden for institutions. Because of this, we have identified the critical elements to allow suppliers to disclose their security practices, procedures, and policies in a consistent tool for institutions to make their process more efficient.
Note: The 1EdTech TrustEd Apps Security Vetting rubric does not address all security concerns that districts/institutions will have. The rubric is meant to establish a baseline of criteria and questions that should be asked when reviewing a digital resource.
Criteria
Those who review potential apps for use at institutions should understand the difficulty for an app supplier to include all of the requirements of this rubric or the specific criteria important to the institution in question. It is, therefore, crucial to not only review the security policy but also attempt to reach out to the app supplier and communicate any questions and/or concerns about what may and may not have been found in the policy. Reviewers should take a “If you see something, say something” approach. By communicating with the supplier, reviewers will get a more thorough and accurate review of the app while helping to improve their own security practices and transparency, helping countless others. Communication with the supplier helps clarify any misunderstandings and interpretations of statements made in the policy. This allows for open communication that will help institutions understand common language that suppliers must use in their policies and also assists suppliers in simplifying the language in their policies that could be misinterpreted.
The Rubric contains these four core sections that are essential to do a base level review of a digital resource:
- Documentation & Company Information
- Data
- Systems Management
- Third Party Assessment
The Rubric also contains three qualifying columns that establish how well a digital resource aligns with district/institutional standards:
- Does Not Meet Expectations: The policy does not meet the criteria established by the rubric.
- Reservations: The policy is unclear as to what it may or may not do as established by the criteria in the rubric.
- Meets Expectations: The policy fully meets or exceeds the criteria established by the rubric.
The App Vetting Process
Overview
This rubric is a supplier self-review. It has been developed by the TrustEd Apps Security Task Force which is composed of experts from institutions and suppliers. This multi-year project included reviewing existing vetting tools, best practices, and input from institutions and suppliers through a pilot and at relevant professional organizations.
Specifically, the rubric covers four key areas including Documentation & Company Information, Data, Systems Management, and SelfAssessment.
- The Documentation & Company Information section: Provides crucial foundational information to better understand a supplier’s organizational structure, policy, and history.
- The Data section: Allows institutions to understand where data is stored, how it is handled, and what type is included.
- The Systems Management section: Provides information about the availability of access controls, systems used by the supplier, and log availability.
- The Third Party Assessment section: Provides an opportunity to share which third parties are involved and if they have completed any third party assessments.
Goals
The TrustEd Apps Security Vetting review and publishing process helps institutions and suppliers understand and address security concerns in a cooperative manner:
- Supplier self reviews are submitted.
- Apps will have a quality check by 1EdTech staff prior to publishing
- Reviews remain valid for 1 year
- Suppliers may re-submit a self-evaluation of their apps when changes have been made to their policies.
This process differs from other existing app vetting approaches because it promotes open communication about supplier products within the 1EdTech trusted membership community. This open line of communication allows suppliers and districts/institutions to work together to provide an accurate review of the organization's products.
In addition, the open collaboration between districts/institutions and suppliers promotes transparency that helps all 1EdTech members understand the various components of privacy and terms of service policies and why they are necessary.
Who Can Submit Reviews
The TrustEd Apps Security Rubric is designed as a self-evaluation rubric to be completed by a representative of the supplier. As such, suppliers will submit reviews of their products to 1EdTech for publishing. Once posted, all vetted app reviews can be viewed by other 1EdTech Members and Staff. The app vetting report itself will be viewable under the product’s entry in the TrustEd Apps Directory and TrustEd Apps Management Suite.
Governance & Recourse
- Suppliers can submit their own self reviews of their products.
- 1EdTech receives a notification for every review submitted.
- All reviews are initially unpublished until 1EdTech provides a quality assurance check, then they are published.
- If feedback is received, 1EdTech will communicate with the supplier to clarify the area related to the feedback on the self-assessment
- If a supplier’s product or accessibility policy has changed significantly, it may not match an existing review which had been previously submitted. In that case, suppliers may submit a note for 1EdTech to attach to an existing review. Suppliers may also ask for their now outdated reviews to be removed.
- On an annual basis, suppliers will be notified to review completed reviews to determine if updates are needed.
The Quality Assurance Check
The Quality Assurance Check will consist of the following:
- 1EdTech provides a quality check.
- Review each section, note concerns and questions to raise to the supplier to ensure clarity.
- Review any client feedback comments.
- Ensure that the supplier is aware of any client feedback submitted.
Expiration Procedure
- All reviews, regardless of its outcome, are deemed invalid after a year.
- When a supplier leaves 1EdTech, any reviews conducted on that supplier's products will no longer be available in the product directory.
Notification & Versioning
-
The latest rubric version will be posted on the 1EdTech website.
-
For clarity in product reviews, rubric versions should be kept consistent for a year. 1EdTech will send an email to the members with major changes to the rubric. Minor changes, such as corrections for typos, usually don’t need notification;
-
Changes to the rubric will not affect existing ratings in the product directory - because each review lists the version of the rubric which was used;
-
When a new rubric version is released, it should be used for any new reviews for the upcoming year;
-
The following process will be used for making updates to the rubric:-
- The TrustEd Apps Security Task Force will review changes on an annual basis for major changes
- Minor changes, such as corrections for typos, could be requested and updated directly by 1EdTech during the year
- Changes to the rubric will need to go through an approval process to draft and approve a new spec document, according to 1EdTech Technical Board Policies and Procedures.
The Rubric
The following tables show each question with specific language which should be used as the evaluation criteria for vetting apps.
1EdTech TrustEd Apps Security Practices Rubric
| Item# |
Documentation and Information
|
Does Not Meet Expectations
|
Reservations
|
Meets Expectations
|
Related HECVAT LITE Rubric Items
|
|---|---|---|---|---|---|
| DOC-01 | Have you undergone an external audit? | Has not undergone an external audit. | * Has undergone and external audit but cannot share the results. * Has not undergone an external audit but has completed the HECVAT. * Has not undergone an external audit but is in the process of completion. |
Has undergone an external audit and can share the audit results or certificate | DOCU-01 Have you undergone a SSAE 18/SOC 2 audit? |
| DOC-02 | Do you conform with a specific industry standard security framework? (e.g. NIST Cybersecurity Framework, CIS Controls, ISO 27001, etc.) | Does not conform with any specific industry standard. | Conforms with a specific industry standard but cannot provide evidence of conformance. | Conforms with a specific industry standard and can show evidence of conformance. | DOCU-04 Do you conform with a specific industry standard security framework? (e.g. NIST Cybersecurity Framework, CIS Controls, ISO 27001, etc.) |
| DOC-03 | Does your organization have a documented data privacy policy? | No | Yes | The documented policy is presented to users and their personal data is only used to provide the service. | DOCU-07 Does your organization have a data privacy policy? |
| DOC-04 | Do you have a documented, and currently implemented, employee onboarding and off boarding policy? | No | There's a documented informal policy or procedure. | Yes | DOCU-08 Do you have a documented, and currently implemented, employee onboarding and off boarding policy? |
| DOC-05 | Do you have a well documented Disaster Recovery Plan (DRP) that is tested annually? | No | There's a documented informal plan or procedure. | Yes | QUAL-04 Do you have a well documented Disaster Recovery Plan (DRP) that is tested annually? |
| DOC-06 | Do you have a documented and currently followed change management process (CMP)? | * Does not have a documented CMP * Does not follow CMP |
Follows a CMP but does not have a fully documented CMP. | Has a fully documented process & process is followed and includes a change log. | DOCU-09 Do you have a documented change management process? |
| DOC-07 | Have you had a reportable breach in the last 5 years? | Previous breaches were not handled in a transparent manner. | Any breaches were reported to the institutions and mitigated in an acceptable time frame. | No reportable breaches in the last 5 years. | CO-02 in HECVAT is “Have you had an unplanned disruption to this product/service in the last 12 months? |
| DOC-08 | Do you have a dedicated Information Security staff or office? | Does not have a dedicated information security staff or office. | * Small organization with a single dedicated person responsible for information security * Information Security responsibilities are contracted out |
Has a fully dedicated Information Security staff or office. | Has a fully dedicated Information Security staff or office. Do you have a dedicated Information Security staff or office? |
| DOC-09 | Do you follow dev ops practices? | Does not have a dedicated development team. | Has a dedicated software & system development team but security is not a focus of the team. | Follows devsec ops practices. | COMP-04 Do you have a dedicated Software and System Development team(s)? (e.g. Customer Support, Implementation, Product Management, etc.) |
| DOC-10 | Can you share the organization chart, mission statement, and policies for your information security unit? | Does not share organization chart, mission statement, and policies for the information security unit? | Is willing to share some but not all of the requested information (see notes to clarify what information is shared). | Has an organization chart, mission statement, and policies for the information security unit and is willing to share. | PPPR-01 Can you share the organization chart, mission statement, and policies for your information security unit? |
| DOC-11 | Are information security principles designed into the product lifecycle? | Information security principles are not designed into the product lifecycle. | Information security principles are designed into the product lifecycle and tested against security requirements at each functional code revision. | PPPR-04 Are information security principles designed into the product lifecycle? |
|
| DOC-12 | Do you have a documented information security policy? | No | Yes | PPPR-11 Do you have a documented information security policy? |
|
| DOC-13 | Do you have a formal incident response plan? | No | Yes, but plan does not state or require updates or training. | Yes and regularly exercised and people are regularly trained. | IH-01 Do you have a formal incident response plan? |
| DOC-14 | Do you carry cyber-risk insurance? | No | Yes, but level of coverage may not be sufficient to cover institution minimum. | Yes | IH-04 Do you carry cyber-risk insurance to protect against unforeseen service outages, data that is lost or stolen, and security incidents? |
| DOC-15 | Do you have either an internal incident response team or retain an external team? | No | Organization uses only an internal or external response team but not both. | Yes, both internal and external. | IH-02 Do you have either an internal incident response team or retain an external team? |
| DOC-16 | What is your capability to respond to incidents? | None | Yes, but only during business hours. | Yes 24x7x365 | IH-03 Do you have the capability to respond to incidents on a 24x7x365 basis? |
| Item# |
Data
|
Does Not Meet Expectations
|
Reservations
|
Meets Expectations
|
Related HECVAT LITE Rubric Items
|
|---|---|---|---|---|---|
| DA-01 | Does the environment provide for dedicated single-tenant capabilities? | No | Yes | DATA-01 Does the environment provide for dedicated single-tenant capabilities? If not, describe how your product or environment separates data from different customers (e.g., logically, physically, single tenancy, multi-tenancy). |
|
| DA-02 | Is data encrypted in transport? (e.g. system-to-client, system-to-system)? | No | Yes | DATA-03 Is sensitive data encrypted, using secure protocols or algorithms, in transport? (e.g. system-to-client) |
|
| DA-03 | Is sensitive data encrypted, using secure protocols or algorithms, in storage? (e.g. disk encryption, at-rest, files, and within a running database)? | Data not encrypted at rest. | Not all data encrypted at rest. | All data encrypted at rest. | DATA-04 Is sensitive data encrypted, using secure protocols or algorithms, in storage? (e.g. disk encryption, at-rest, files, and within a running database) |
| DA-04 | Do you have a media handling process, that is documented and currently implemented, including end-of-life, repurposing, and data sanitization procedures? | No | Yes, partially documented/implemented. | Yes, has all of the above. | DATA-19 Do you have a media handling process, that is documented and currently implemented that meets established business needs and regulatory requirements, including end-of-life, repurposing, and data sanitization procedures? |
| DA-05 | Will data regulated by PCI DSS reside in the vended product? | Any data directly collected cannot be used. | Fully meets PCI DSS requirements. | QUAL-05 Is the vended product designed to process or store Credit Card information? |
|
| DA-06 | Are you able to accommodate storing each institution's data within their desired geographic region? | No | Possibly, due to limited options for geographic regions. | Yes | DCTR-02 Are you generally able to accommodate storing each institution's data within their geographic region? |
| DA-07 | Does the hosting provider have a SOC 2 Type 2 report available? | No compliance doc about meeting controls. | Has a review of controls, but not SOC 2. | Has SOC 2 | DCTR-01 Does the hosting provider have a SOC 2 Type 2 report available? |
| Item# |
Systems Management
|
Does Not Meet Expectations
|
Reservations
|
Meets Expectations
|
Related HECVAT LITE Rubric Items
|
|---|---|---|---|---|---|
| SM-01 | Do you have a systems management and configuration strategy that encompasses servers, appliances, cloud services, applications, and mobile devices (company and employee owned)? | No | Yes, but not for all of the systems listed (use notes to clarify which systems are covered or break it into smaller subquestions). | Yes | CHNG-15 Do you have a systems management and configuration strategy that encompasses servers, appliances, cloud services, applications, and mobile devices (company and employee owned)? |
| SM-02 | Will the institution be notified of major changes to your environment that could impact the institution's security posture? | No | Yes, but only after change. | Yes, prior to change. | CHNG-03 Will the institution be notified of major changes to your environment that could impact the institution's security posture? |
| SM-03 | Are you utilizing a stateful packet inspection (SPI) firewall? | No | Yes and alerts are actioned. | FIDP-01 Are you utilizing a stateful packet inspection (SPI) firewall? |
|
| SM-04 | Do you use an automated IDS/IPS system to monitor for intrusions? | No | Yes | FIDP-04 Have you implemented an Intrusion Detection System (network-based)? FIDP-05 Have you implemented an Intrusion Prevention System (network-based)? |
|
| SM-05 | Do you require direct connectivity to the Institution's network for support, administration or access into any existing systems for integration purposes? | Requires direct connectivity all of the time with no review. | Yes, we require direct connectivity. | Any direct connectivity we require will be for limited periods of time and will be fully monitored by the institution. | |
| SM-06 | Do you support access control (e.g. RBAC, ABAC, PBAC) for end-users? | No | Yes, but only separates teachers and students. | Provides separation of at a minimum students, teachers/faculty and teaching assistants. | APPL-01 Are access controls for institutional accounts based on structured rules, such as role-based access control (RBAC), attribute-based access control (ABAC) or policy-based access control (PBAC)? |
| SM-07 | Do you support access control (RBAC, ABAC, or PBAC) for system administrators? | No | Yes, but not customizable for specialized admin types. | Yes, it is fully customizable and can provide evidence. | APPL-02 Are access controls for staff within your organization based on structured rules, such as RBAC, ABAC, or PBAC? |
| SM-08 | Do you control and audit employee access to customer data? | No | Controlled but not audited. | Yes to both. | APPL-10 Do you have a fully implemented policy or procedure that details how your employees obtain administrator access to institutional instance of the application? |
| SM-09 | Does the system provide data input validation? | No | Yes, provides input validation but does not meet all OWASP guidelines. | Yes, follows OWASP guidelines. | APPL-03 Does the system provide data input validation and error messages? |
| SM-10 | Are you using a web application firewall (WAF)? | Does not utilize a web application firewall (WAF). | Utilizes a web application firewall (WAF) but alerts are not actioned. | Utilizes a web application firewall (WAF) and alerts are actioned. | APPL-04 Are you using a web application firewall (WAF)? |
| SM-11 | Do you subject your code to static code analysis and/or static application security testing prior to release? | No | Conducts a peer review but does not use an external tool. | Yes | APPL-13 Do you subject your code to static code analysis and/or static application security testing prior to release? |
| SM-12 | Do you enforce MFA for vendor administrative access? | No MFA or other password controls. | No MFA but has strong password controls that aligns with NIST recommendations. | Uses MFA | DCTR-15 Are you requiring multi-factor authentication for administrators of your cloud environment? |
| SM-13 | Does your solution support single sign-on (SSO) protocols for user and administrator authentication? (e.g. InCommon) | Does not provide SSO for Institutional users and administrators. | Uses SSO for Institutional users and administrators but it is not institution approved. (e.g. Google or Social Media login option) | Does provide a Institution approved SSO for Institutional users and administrators. | AAAI-01 Does your solution support single sign-on (SSO) protocols for user and administrator authentication? |
| SM-14 | Are audit logs available to the institution that include AT LEAST all of the following; login, logout, actions performed, timestamp, and source IP address? | Audit logs are not available. | Audit logs include all of the following; login, logout, actions performed, and source IP address only by formal request. | Audit logs include all of the following; login, logout, actions performed, and source IP address and are available in admin dashboard. | AAAI-17 Are audit logs available that include AT LEAST all of the following; login, logout, actions performed, and source IP address? |
| SM-15 | Can your system auto provision accounts through SSO? | No | System can restrict access to SSO mechanisms but it isn't flexible. | Yes | |
| SM-16 | Do you support differentiation between email address and user identifier? | No | Yes, but does not enforce it. | Yes and enforces it. | AAAI-10 Do you support differentiation between email address and user identifier? |
| Item# |
Third Party Assessment
|
Does Not Meet Expectations
|
Reservations
|
Meets Expectations
|
Related HECVAT LITE Rubric Items
|
|---|---|---|---|---|---|
| TP-01 | Will institution data be shared with or hosted by any third parties? | Shared for any reason other than to offer the service. | Purposeful sharing to benefit learner and/or institution which is disclosed to institution for review and approval. | Shared and/or hosted only to provide service. | QUAL-02 Will institution data be shared with or hosted by any third parties? (e.g. any entity not wholly-owned by your company is considered a third-party) |
| TP-02 | Do you perform security assessments provided of third party companies with which you share data? (i.e. hosting providers, cloud services, PaaS, IaaS, SaaS, etc.). | No | Yes | THRD-01 Do you perform security assessments of third party companies with which you share data? (i.e. hosting providers, cloud services, PaaS, IaaS, SaaS, etc.). |
|
| TP-03 | Have your systems and applications had a third party security assessment completed in the last year? | No | Has an internal assessment and can provide the results. | Yes, has a 3rd party assessment and can provide high level results and gives organization's name. | VULN-02 Have your systems and applications had a third party security assessment completed in the last year? |
References
-
HECVAT. Retrieved from (https://library.educause.edu/resources/2016/10/higher-education-community-vendor-assessment-toolkit)
-
Educause Higher Education Community Vendor Assessment Toolkit https://library.educause.edu/resources/2016/10/higher-education-community-vendor-assessment-toolkit
Informative References
- National Institute of Standards and Technology (NIST). May 2023 URL: https://csrc.nist.gov/glossary/term/at
- International Business Machines (ibm). May 2023 URL: https://www.ibm.com/docs/en/strategicsm/10.1.3?topic=security-data-rest-encryption
- Ericsson. May 2023 URL: https://www.ericsson.com/en/blog/2019/8/why-is-automated-provisioning-so-important
- Techtarget. May 2023 URL: https://www.techtarget.com/searchcio/definition/change-management
- Unitrends. May 2023 URL: https://www.unitrends.com/blog/cis-controls
- Techopedia. May 2023 URL: https://www.techopedia.com/definition/29017/cloud-services
- Court Services Online. May 2023 URL: https://www.csoonline.com/article/3643054/cyber-insurance-explained.html
- Digital Guardian. May 2023 URL: https://www.digitalguardian.com/blog/what-data-encryption
- Law Insider. May 2023 URL: https://www.lawinsider.com/dictionary/data-transport
- Nextlabs. May 2023 URL: https://www.nextlabs.com/what-is-data-segregation/
- Redhat. May 2023 URL: https://www.redhat.com/en/topics/devops/what-is-devsecops
- Merriam-Webster. May 2023 URL: https://www.merriam-webster.com/dictionary/end%20user
- Service Express. May 2023 URL: https://serviceexpress.com/resources/eol-eosl-tip-sheet/
- Emeritus. May 2023 URL: https://emeritus.org/in/learn/information-security-and-its-principles/
- Cynet. May 2023 URL: https://www.cynet.com/incident-response/incident-response-team-a-blueprint-for-success/
- IT Governance. May 2023 URL: https://www.itgovernance.co.uk/iso27001
- Info Savvy. May 2023 URL: https://info-savvy.com/iso-27001-annex-a-8-3-media-handling/
- Federal Trade Commission (FTC). May 2023 URL: https://www.ftc.gov/business-guidance/small-businesses/cybersecurity/nist-framework
- Open Worldwide Application Security Project (OWASP). May 2023 URL: https://owasp.org/
- Atlassian. May 2023 URL: https://www.atlassian.com/agile/product-management
- Tech Slang. May 2023 URL: https://www.techslang.com/definition/what-is-a-security-framework/
- Checkpoint URL: https://www.checkpoint.com/cyber-hub/cyber-security/what-is-soc-2-compliance/
- Aruba Network. May 2023 URL: https://www.arubanetworks.com/techdocs/AOS-CX/10.10/HTML/fundamentals_83xx-10000/Content/Chp_IfaceCfg/sin-sou-ip-add-10.htm
- Fortinet. May 2023 URL: https://www.fortinet.com/resources/cyberglossary/single-sign-on
- Synopsys. May 2023 URL: https://www.synopsys.com/glossary/what-is-sast.html
1. Conformance Statements
As well as sections marked as non-normative, all authoring guidelines, diagrams, examples, and notes in this specification are non-normative. Everything else in this specification is normative.
The key words MAY, MUST, MUST NOT, OPTIONAL, RECOMMENDED, REQUIRED, SHALL, SHALL NOT, SHOULD, and SHOULD NOT in this document are to be interpreted as described in [RFC2119].
An implementation of this specification that fails to implement a MUST/REQUIRED/SHALL requirement or fails to abide by a MUST NOT/SHALL NOT prohibition is considered nonconformant. SHOULD/SHOULD NOT/RECOMMENDED statements constitute a best practice. Ignoring a best practice does not violate conformance but a decision to disregard such guidance should be carefully considered. MAY/OPTIONAL statements indicate that implementers are entirely free to choose whether or not to implement the option.
A. References
A.1 Normative references
- [RFC2119]
- Key words for use in RFCs to Indicate Requirement Levels. S. Bradner. IETF. March 1997. Best Current Practice. URL: https://www.rfc-editor.org/rfc/rfc2119
B. List of Contributors
The following individuals contributed to the development of this document:
| Name | Organization | Role |
|---|---|---|
| Susan Haught | 1EdTech Consortium, Inc. | Editor |
| Jon Werth | Minnesota State (College and University System) | |
| James Williamson | University of California System | |
| Alex Dunlop | Central Piedmont Community College | |
| Daisy Bennett | Instructure | |
| Brian Kelly | EDUCAUSE | |
| Sue McGlashan | Unversity of Toronto | |
| Brent Shaw | Univeristy of Central Florida | |
| Samba Diop | Georgie Institute of Technology | |
| Dale Johnson | University of Wisconnsin System Administration | |
| Scott Wojtanowski | Minnesota State (College and University System) | |
| Mark Leuba | 1EdTech Consortium, Inc. | |
| Markus Gylling | 1EdTech Consortium, Inc. | |
| Kevin Lewis | 1EdTech Consortium, Inc. | |
| Kelly Hoyland | 1EdTech Consortium, Inc. |